I recently wrote about the coincidental (or not) similarities between the Corona virus and cyber security. The more that COVID is with us, the more similarities with cyber I can’t help but see. And by this I mean, the way in which a country should deal with the threat of COVID, is very similar to the way in which an organisation should deal with cyber security threats.
As a recap, the first article covered how important hygiene is in both subjects, and how a consistent methodology or process can help build a better immune system, or security posture.
Here, we will cover some additional but also necessary elements for addressing both subjects – the key one to be discussed is measurements. Someone intelligent once said “what gets measured gets managed”. They also stressed the importance of measuring the right things.
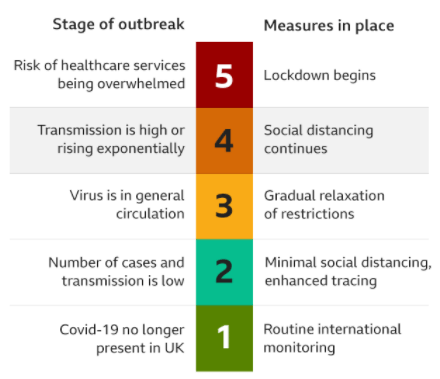
The UK government recently introduced a Corona alert system in which the current level of virus control methods are based on the readings of key measures such as the rate of infection (R rate), number of new cases and deaths and a few others.
They have defined the worst case scenario, a risk which sees the NHS overwhelmed leading to more cases that can be handled effectively and therefore more deaths than what is within reasonable appetite.
This worst case scenario gives us the highest alert level – level 5. Each level below has a threshold of certain measurements mentioned above, and specific guidelines and restrictions in line with the level, i.e. severity of the virus. The UK government then set a conditional plan to resume ‘semi-normal’ living conditions, based on the measurements being at specific thresholds over time.
For example. If the rate of infection remains between 0.5 and 1, the alert level of three, means people can leave the house as much as they like, given that they still keep to guidelines around social distancing.
Here is what it looks like:
In much the same way as a pandemic virus spreads through the world, continually adapting and impacting countries in different ways, cyber security threats do the same. Not only does each organisation have it’s own catalogue of threat actors depending on it’s industry, location, use of technology etc. it also should adapt it’s security controls according to what is happening internally, as well as externally.
I once worked for a company who increased their cyber security control environment directly in line with the level of risk associated with their technology environment. They were a medium sized financial company who at the time didn’t have anything close to the fancy banking features of the leading banks. So the Head of Infosec, my boss at the time, proposed and agreed with the board that when certain features such as current accounts are put in place, the threats will likely increase by X and therefore the control environment should also increase by Y.
This may seem simple and obvious, but this company is the only one out of the five I worked for (and one of those was a security operations centre), who had a predetermined process for increasing cyber security control ability with technological ability and consequential threats.
Taking this way of thinking a step further, organisations should consider applying similar measures to what is happening internally and externally by measuring certain key performance indicators (KPI’s) and statistics from external sources.
KPI’s of course will directly measure results associated with the organisations controls, which are arguably more useful than external statistics such as those provided by vendors. An example of an internal KPI could be the percentage of employees who click on a planned mock phishing campaign. If that percentage exceeds a threshold or risk appetite level, the communications, training and awareness could be immediately reviewed. This is especially useful if phishing campaigns are a key threat to your organisation – wire fraud, for example.
A KPI such as the above can be set for those controls which are the most important for an organisation, depending on its threat landscape and control maturity.
Better still, measure a control which is directly impacted by the external threat environment, whilst also measuring the internal controls. Sticking with the phishing example, you could have a KPI for the number of genuine phishing emails which are reported monthly. This can be disparate at times, but will give you an idea of how well educated employees are, vs. the sophistication of modern social engineering attacks.
Moving away from training and awareness controls, you could set a KPI for the percentage of devices with a critical vulnerability older than 30 days. Or, the percentage of devices which become infected with malware per month.
These all take the external threat environment into consideration, whilst measuring internal control effectiveness. And with each, thresholds can be set to change or at least review the control depending on the performance.
No KPI or other measurement is fullproof, highlighting the importance of measuring many varying controls, and measuring them consistently. If organisations applied something like the UK Government Corona alert system to their security environments, they could stand a better chance at preventing, detecting and responding to today’s cyber security threats.
If you would like to have a chat about your security environment, feel free to reach out.

Leave a comment